CSC 254/454 Fall 2018
Programming Language Design and Implementation
Course description and prerequisites
Teaching Staff and Office Hours:
- Prof. Chen Ding, Fridays 11am to 12pm in Wegmans Hall 3407, x51373.
- Alan, 12pm-1pm Friday, Wegmans 2215
- Alex, 11am-12 Thursday, Wegmans 3201
- Jason, 12:30pm-1:30pm Tuesday, Hylan 301 (CS Minor’s Lab)
- Jie, 2pm-4pm Tuesday, Wegmans 2311
- Michael, 9am-10am Wednesday, Hylan 301 (CS Minor’s Lab)
- Princeton, 12:45pm-1:45pm Wednesday, Hylan 301 (CS Minor’s Lab)
- Wei, 4pm-6pm Tuesday, Wegmans 2602
- Wentao, 3pm-5pm Wednesday, Wegmans 2207
Help Sessions
- 5pm to 6pm Wednesday, Gavett 301
- 3:30pm to 4:30pm Thursday, Wegmans 1009
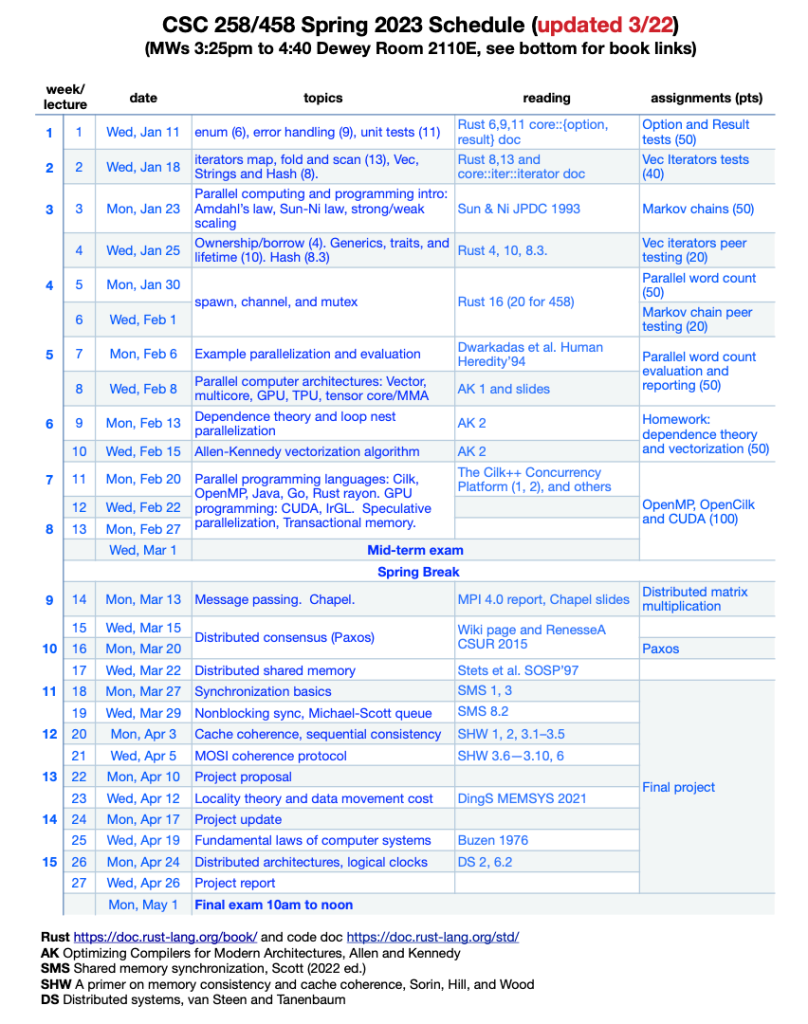
Course Schedule and Handouts (online access at learn.rochester.edu > CSC 254 > Handouts)
The initial schedule can be accessed here. See learn.rochester.edu for the most recent version. Contact the instructor if you have problem accessing the site.
Grading (tentative):
- attendance and pop quizzes, 10%
- mid-term and final exam, 15% and 20% of the remaining 90%
- assignments and projects, 65% of the remaining 90%
Textbooks
Other Materials
No Starch Press
April 2011, 400 pp.
ISBN-13: 978-1-59327-283-8
Web page for 2017 course taught by Prof. Scott.
Policies for CSC 2/454
The workload will be heavy. Be sure to read instructions carefully, start the assignment early, know where/when to seek help, and work with peers.
For group projects, in most cases all students receive the same grade for the group. Team membership may be self-selected or assigned. If you prefer, there is a possibility to work alone. Contact the TA in charge.
Grades will be released periodically to Blackboard, the University’s on-line course management system.
Attendance and Class Participation
Class attendance is mandatory. Please arrive on time. I expect to start at 10:25 sharp, and late arrivals disturb the folks who are already there. I also plan to start many classes with a quiz.
My goal is to spend class time answering questions and explaining material in ways that complement the text. In other words, lecture should complement the text, not rehash it. This means, of course, that reading is mandatory, and must be completed before the corresponding lecture. If no one has questions or suggested discussion topics, I will call on you—so be prepared!
As a general rule, if there’s something you don’t understand, make me stop and explain it. There are probably a dozen people sitting around you who didn’t understand it either, but don’t have the nerve to say so. Likewise, if I’m belaboring something that everyone understands, prod me to move on.
Prof. Scott has made his lecture notes available on-line, but keep in mind that the exams may include topics covered in class, even if they are not in the text book or lecture notes.
Project Help Sessions
The time and location are fixed each week. Attendance is voluntary. There are two sessions each week covering the same topics, which will be given in announcements at the beginning of the week.
No Late Assignments
It is my strict policy not to accept late assignments. Exceptions will be made only by the instructor. Note, however, that I am extremely generous with partial credit, so turn in what you have.
Every semester I have students who let a due date pass. When I ask them what happened they say “Oh, I didn’t finish, so I didn’t turn anything in.” Then I have to give them a zero. If they had turned in even some reasonable preliminary thoughts on how they might have done the assignment—without a single line of code—they often could have received as much as 30% of the total points. This can easily make the difference between letter grades at the end of the semester.
So if it looks like you aren’t going to make a due date, don’t keep debugging down to the wire. Stop an hour early and take the time to organize what you have and put together a write-up that presents it in the best possible light. Your transcript will love you for it.
Academic Honesty
Student conduct in CSC 2/454 is governed by the College Academic Honesty Policy, the Undergraduate Laboratory Policies of the Computer Science Department, and the University’s Acceptable Use Policy for Information Technology. I helped to draft some of the descriptions. I believe in them strongly, and will enforce them aggressively.
The following are details specific to CSC 2/454.
Exams and quizes in CSC 2/454 must be strictly individual work.
Collaboration on programming assignments among team members is of course expected. Collaboration on assignments acrossteams is encouraged at the level of ideas. Feel free to ask each other questions, brainstorm on algorithms, or work together at a whiteboard. You may not claim work as your own, however, unless you transform the ideas into substance by yourself. Among other things, this means that you must leave any brainstorming sessions with no written or electronic notes—only what you carry in your head.
If you use the work of others (e.g., you download a function from the web at the last minute so that you can get the rest of your project working), then (1) either you must have the author’s explicit permission or the material must be publicly available, and (2) you must label what you copied, clearly and prominently, when you hand it in. You will of course get points only for the parts of your assignment that you wrote yourself.
To minimize the temptation to steal code, all students are expected to protect any directories or on-line repositories in which they do their work.
For purposes of this class, academic dishonesty is defined as
- Any attempt to pass off work on an exam or quiz that didn’t come straight out of your own head.
- Any collaboration on assignments beyond the sharing of ideas, unless the collaborating parties clearly and prominently explain exactly who did what, at turn-in time.
- Any activity that has the effect of significantly impairing the ability of another student to learn. Examples here might include destroying the work of others, interfering with their access to resources, or deliberately providing them with misleading information.
Note that grades in CSC 2/454 are assigned on the basis of individual merit rather than relative standing, so there is no benefit—even a dishonest one—to be gained by sabotaging the work of others.
I work under the assumption that students are honest. I will not go looking for exceptions. If I discover one, however, I will come down on it very hard. Over the past few years, I have submitted about a dozen cases to the College Board on Academic Honesty. All resulted in major penalties for the students involved.